From remote network attacks to the manufacture of counterfeit products, the spread of security threats has become more widespread, affecting all industries. Once these threats are successful, they mean huge losses in recovery costs and service revenues. Of course, the most obvious is the loss of brand equity. Therefore, it is critical to implement strong security features in new and existing designs to protect intellectual property (IP) and enable trusted authentication for networked devices. To protect against these threats, Microchip Technology Inc. has announced the availability of the ATECC608A CryptoAuthenticationTM device, which developers can use to add hardware-based security features to their designs. Microchip has also established a Security Design Partner Program to help developers connect with third-party partners to enhance and accelerate security design.
The basis of secure communication is the ability to create, protect, and authenticate devices that are unique and trusted. By separating the device's private key from the system, placing it in a secure area, and combining industry-leading encryption, the ATECC608A provides a high level of security for almost any type of design. Key features of ATECC608A include:
Best-in-class key generation: The Federal Information Processing Standard (FIPS)-compliant random number generator (RNG) generates a unique key that meets the latest requirements of the National Institute of Standards and Technology (NIST) and is FIPS-certified for the entire system. Provides an easier way.

Boot verification for small systems: The new command facilitates signature verification and digest calculations for systems using small MCUs (such as ARM? Cortex?-M0+) and more robust embedded system master microcontroller (MCU) firmware.
Trusted Authentication for LoRa Nodes: The AES-128 engine enables secure deployment of LoRa infrastructure by enabling authentication of trusted nodes in the network.
Fast Encryption Processing: Hardware-based integrated elliptic curve cryptography (ECC) algorithms enable faster and more secure creation of smaller keys and establish certificate-based trusted roots compared to other implementations that rely on traditional methods.
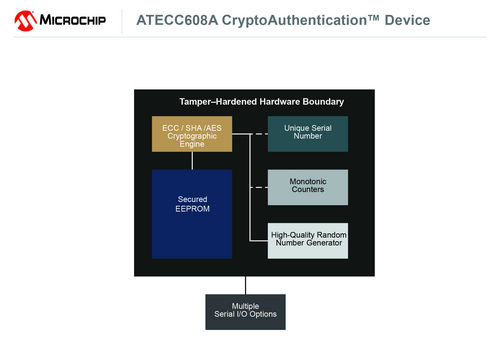
Tamper-proof protection: Tamper-proof technology protects keys from physical attacks and prevents intrusion attempts after deployment. These technical support systems maintain secure and trusted identity information.
Configuration in Trusted Manufacturing: Companies can use Microchip 's secure manufacturing facilities to securely configure their keys and certificates, thereby avoiding the risk of leaks in the manufacturing process.
NuriDagdeviren, vice president of security products at Microchip, said: "For today's networking applications, security is essential, especially for applications ranging from hardware to the cloud. As a result, Microchip offers proven hardware security solutions and leads. The cloud provider has built an unprecedented partnership to provide all of the building blocks for our customers to build security solutions to help them protect their IP, brand value and revenue streams."

In addition to providing a hardware security solution, customers can join Microchip's Security Design Partner Program. These industry-leading companies, including Amazon Web Services (AWS) and Google Cloud Platform, provide complementary cloud-driven security models and infrastructure. Other partners are well versed in implementing Microchip's security devices and libraries. Whether designers want to protect Internet of Things (IoT) applications or add authentication capabilities to consumables such as ink cartridges or accessories, with the expertise of security design partners, they reduce development costs and time-to-market.
Antony Passemad, director of product management for Google Cloud IoT, said: "By working with Microchip, the work done on the ATECC608A chip has enabled Google IoT customers to acquire new products with a high level of security and a very smooth experience."
development tools
Designers who want rapid prototyping of security solutions can use the new CryptoAuthXplainedPro Evaluation and Development Kit (ATCryptoAuth-XPRO-B), a plug-in board that is compatible with all MicrochipXplained and XplainedPro evaluation boards.
Supply
The ATECC608A10,000 is available in volume quantities. The ATCryptoAuth-XPRO-B plug-in development board is available now.
A TPU Screen Protector made of the super toughness of the honeycomb structure. Its unique ultra-soft properties allow it to cover the most complex curves and contours in a device.
The self-healing design of the Hydrogel Screen Protector can protect the display screen of the device from damage, leave no air bubbles, and maintain the sensitivity of the touch screen. Advanced anti-fingerprint and dust- and oleophobic overlays keep your screen smudge- and dirt-free. This overlay is also important in providing maximum touch sensitivity for improved high-speed glide and optimal touch response.
The optical transparency of the Hydrogel Film is more than 90%, showing you the most original screen color and bringing the most realistic visual experience.
If you want to know more about the product information of the Hydrogel Screen Protector for vivo, please click the product details to view the parameters, model, picture, price and other information of the vivo Screen Protector.
Whether you are a group or an individual, we will do our best to provide you with accurate and comprehensive information about Hydrogel Screen Protectors!
Screen Protector For vivo,Hydrogel Screen Protector For vivo,Hydrogel Film for vivo,TPU Screen Protector For vivo
Shenzhen Jianjiantong Technology Co., Ltd. , https://www.jjtbackskin.com