
NSA is black! ? no no.
The Shadow Broker, the hacker group that issued the news, only claimed that they had invaded the “Equation Group†and they leaked most of the hacking tools they had obtained from the hacker’s computer system. On the Internet, and told everyone there are some "quality documents" that need to be paid.
As we all know, the hacking organization equation has an unclear relationship with the NSA. The NSA will certainly not respond to this incident, but Snowden has been unable to bear the question. He has publicly questioned the matter on Twitter, stating that someone deliberately deterred the trap and wanted everyone to think that the U.S. government has participated in many hackers. action.
There is no further progress in the current incident. Let us take a look at this hacking organization that is inextricably linked with the NSA.
According to foreign security experts, hackers organize equation whereabouts can be traced back to 2001, or even earlier, there are signs of living jump in 1996, the number of members of the group more than 60 people. The equation is evaluated as the most secretive, advanced, and most sophisticated hacker organization with a high level of threat.
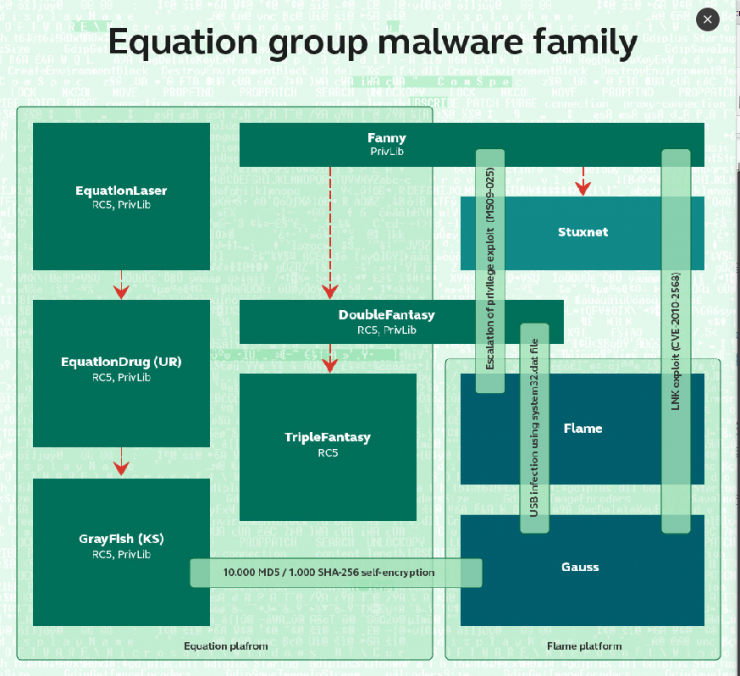
The names of the equations are named after their Kaspersky Lab. Kaspersky said in his report that they call them equations because they prefer to use more complicated technologies such as encryption algorithms and fuzzy strategies in their actions.
Hacker organization equation virus map
According to Kaspersky's analysis report, RC5 encryption algorithm technology runs through the equations to design malware and worms, and some use RC6, RC4, and AES.
The RC5 and RC6 encryption algorithms were developed by Ronald Rivest in 1994 and 1998 respectively. The two algorithms are very similar. RC6 adds an extra value-added algorithm to the key based on RC5, making it more robust. The keys for both encryption algorithms are built using the same mechanisms and constants P and Q.
According to security experts, there are indications that the organization is related to the US National Security Agency. A computer security expert Claudio Guarnieri who believes that the equations are related to the NSA  Once a member of NSA's Prism Portal incident analysis team, he believes that Kaspersky Lab's analysis of exposed malware is now involved in previous security experts' research, although the analysis may be different in depth. Guarnieri had positively told Forbes that the behavior of the equation hacker group was 100% related to the NSA, because some of the organization's high-profile attack action code was very similar to the activity information recorded in the leaked documents in the NSP leak event “Prism Gate†.
The equations rely on a variety of techniques to infect their target of attack. mainly include:
• Self-replicating Fanny worm
• With optical drive and system vulnerabilities
• U disk and system vulnerability
• Network-based attack
Of the many viruses released by the hacking group of equations, the Fanny worm is the most powerful one and can invade networks with gatekeeper isolation. To implement this intrusion attack, they used a unique USB-based control mechanism that allowed attackers to freely access the network that was physically disconnected.
This unique USB control mechanism is mainly achieved through U disk infection. A hidden storage area in the U disk can collect basic system information from the isolated network. When the U disk infected with the Fanniney worm is inserted, the collected information can be immediately sent to the attacker in the networking state. .
If an attacker wants to run an instruction on a network environment that is isolated by a gatekeeper, they can store the instruction in a hidden space on the USB flash drive through a worm. When the U disk is inserted into the target computer, the worm automatically recognizes and runs the instructions.
Of the seven types of attackers that have been detected by Kaspersky Lab's equation hacker group, four are implemented using zero-day vulnerabilities. Among them is the exploit exploit method that Kaspersky Lab has not developed, mainly for Firefox browser with onion routing TOR. Â
Kaspersky Lab also found in analysis and analysis that during the intrusion, the system of equations can exploit ten loopholes in a program chain at one time. However, the total number of worms it attempts to attack the target will not exceed three times. If the first attempt is unsuccessful, the second and third attempts will be followed. If there are no successful attacks after three attempts, they will Will give up attacking this goal.
Another security expert discovered that exploiting the virus that used to disrupt Iran's nuclear plant's uranium enrichment program (Stuxnet) contained the vulnerability intrusion technique of the Fanny worm.
Hacker Organization Equation Virus Attack Atlas
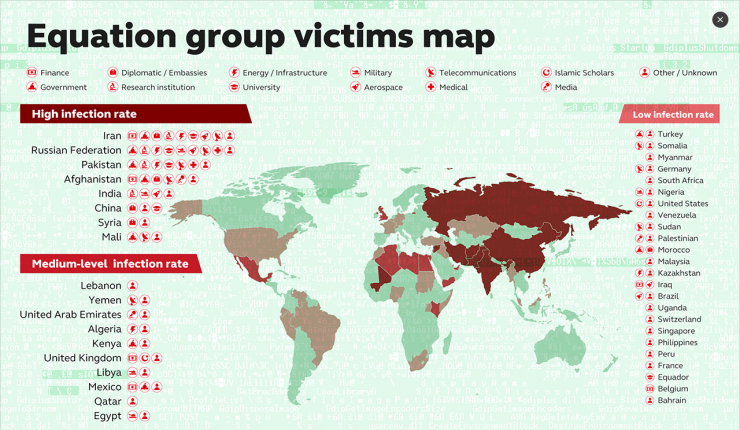
So far, malicious software and worms that have been developed by the equation hacking organizations have infected networks in more than 30 countries around the world. Successfully cracked encryption technologies including government or diplomatic departments, telecommunications, aerospace, nuclear energy, military, finance, and Islamic religious organizations. The taste is so complicated that it has nothing to do with politics?