In today's hyper-connected world, how to protect new designs from cloning, reverse engineering, and/or tampering is a major challenge. FPGA devices help achieve these goals by adding features that meet device-level security requirements.
Growing IoT security needs
The Internet of Things (IoT) can be thought of as consisting of multiple electronic networks that require end-to-end layered security starting at the device level (see Figure 1). To help achieve this layered security, FPGA devices can incorporate unique built-in features and differentiation capabilities, as well as a root of trust in often complex applications.
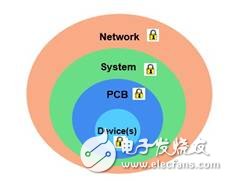
Figure 1 Networked system requires end-to-end layered security starting from the device
The solution uses an FPGA device with embedded security features inside, allowing system architects to plan their security architecture at the core level rather than at a secondary level. A very important issue with many SRAM-based FPGA devices is that each boot must be configured from external memory so that it is easy to get your design through reverse engineering; therefore, a better approach is to use on-chip non-volatile Memory (NVM) FPGAs can store configuration information using NVM events.
Because data security is one of the most important security layers, FPGA devices must protect all data, including the application data being processed. We should consider a variety of data protection features, including hardware protection against differential power analysis (DPA) attacks on sideband channels. Unilateral or differential power analysis (SPA/DPA) can extract the key by measuring its power consumption in the bitstream loading.
A key consideration is the use of physical unclonability (PUF) to generate a public-private key to authenticate the machine. The PUF shown in Figure 2 can be used as a unique "biometric" logo for each device - similar to human fingerprints, no two are identical and unclonable.
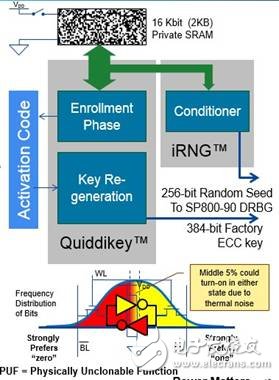
Figure 2 SRAM PUF architecture utilizes quasi-static (quasi-staTIc) random start behavior of SRAM bits
SRAM PUF
The SRAM physical unclonable feature is one of the best features and the most reliable memory PUF type that can be implemented on smart card chips, FPGAs or other IC devices. It works by measuring the random start state of the bits in the SRAM block, each SRAM bit containing two nominally equivalent but not identical cross-coupled inverters. When a power supply is applied to the IC, each SRAM bit is activated to a "1" or "0" state, which is largely dependent on the IC manufacturing process.
When the inverter has a good balance, the thermal noise may overcome the limit of the predetermined reference bit, so that the initial value appears in the opposite state. However, this predetermined state generally overcomes any dynamic noise and can be used to restore the noise-crambled bits to their initial values ​​using error correction techniques, ensuring that the same key is reconstructed each time it is turned on.
The SRAM PUF can be designed to ensure that the key is perfectly reconstructed under all environmental conditions and has a very low error rate throughout the life cycle – as low as one part per billion. In addition, since the key of the SRAM PUF effectively disappears from the device when the power is turned off, it has extremely powerful protection. If the activation code is erased, there is no subsequent analysis to reconstruct the PUF key.
Encryption function
If PUF technology is to be implemented in an FPGA or SoC FPGA device, these devices must have built-in encryption, such as hardware accelerators for AES, SHA, HMAC, and Elliptic Curve Cryptography (ECC), as well as true random bit generation at the encryption level. Device. With these features, it is possible to create a user's public key infrastructure that allows users to authenticate the legitimacy of each machine on the network through their own authorization mechanism. This ensures that each device has a chain of trust that extends from the well-protected root CA key to the high-confidence atomic identity established by the PUF of the FPGA device. The combination of PUF and PKI ensures that each device and its communications are protected and can be used securely and reliably for M2M, IoT and other hyper-connected applications.
Qunsuo are dedicated in Industrial PDA, our PDAs are durable and long time standby. We can provide handheld Barcode Scanner Pda, PDA with built in printer and so on. All of our PDA provide with demo app and free SDK, supporting our customers for use easily. We can provide our customers prompt after-sales service about any technical supports. Our PDA support many functions, including RFID reader, NFC reader, Barcode Scanner, UHF reader, fingerprint scanner, IC card reader, PSAM and etc. And also if you have any PDA OEM/ODM requirements, we can also help you to make prototype into physical.

Industrial PDA
Barcode Scanner Pda,Pda Scanner Android,Pda Printer Scanner,Pda Android 2D Barcode Scanner
Shenzhen Qunsuo Technology Co., Ltd , https://www.qsprinter.com