Research on Network Monitoring Technology Based on ARP Deception
introduction
Most of the current local area networks belong to Ethernet, and the main connection method is to connect through switches. The switch is similar to a hub in appearance, but internally uses the principle of circuit switching to switch the input of one port to another designated port. Switched Ethernet makes up for the shortcomings of shared Ethernet (networks connected with hubs), but it also increases the difficulty of network monitoring to a certain extent. The switch maintains a database table of ARP when working, and the MAC address bound to each port of the switch is recorded in this library. When a packet is sent to the switch, the switch will match the destination MAC address of the packet with its own Compare the ports in the maintained database, and then send the data packets to the corresponding ports. The biggest difference between a switch and a hub is that communication packets are no longer copied to all other ports, but are accurately sent to the port where the target machine is located. Therefore, other machines cannot monitor this more purposeful communication, of course. Unable to capture the data packet. Therefore, we need to find a simple and convenient monitoring and deployment software in switched Ethernet in order to effectively monitor the widely existing switched Ethernet.
1 ARP protocol and spoofing technology
1.1 ARP protocol
IP data packets are often sent over Ethernet. Ethernet devices do not recognize 32-bit IP addresses. They transmit Ethernet data packets at 48-bit Ethernet addresses. Therefore, the IP driver must convert the IP destination address to an Ethernet destination address. There is some static or algorithmic mapping between these two addresses, and it is often necessary to look at a table. The ARP address resolution protocol (Address ResoluTIon Protocol) is responsible for converting the IP address of the network layer into the MAC address of the data link layer, and establishing a one-to-one mapping between the IP address and the MAC address. The basic function of the ARP protocol is to query the MAC address of the target device through the IP address of the target device to ensure smooth communication.
1.2 ARP spoofing technology
Although the ARP protocol is an efficient data link layer protocol, as a LAN protocol, it is built on the basis of mutual trust between hosts, so there are also some security issues. According to these security issues in the ARP protocol, you can use the following methods to spoof ARP:
(1) The attacker can then respond after receiving the ARP request packet and perform counterfeiting.
(2) Since the ARP response packet sent by the fake machine may arrive later than the attacker's response packet, in order to ensure that the attacker's MAC address is stored in the cache of the attacked machine most of the time, you can After receiving the ARP request broadcast, the ARP reply is sent again after a delay.
(3) Due to the different implementations of ARP cache processing by various operating systems, some operating systems (such as Linux) will use non-broadcast ARP requests to cache addresses to request updates to the cache. In a switched network environment, this cache update cannot be captured by other machines, so it is necessary to prevent the host from sending update cache messages.
ARP spoofing technology can realize data monitoring in the full exchange environment. Therefore, we can use this technology to monitor switched Ethernet.
2 Use ARP spoofing technology to capture switched Ethernet data
Through the previous description, we know that switched Ethernet can use ARP spoofing technology for monitoring. The following explains how to use ARP spoofing technology to capture switched Ethernet data.
2.1 ARP protocol implementation
When parsing IP addresses on Ethernet, the format of ARP request and response packets is as shown
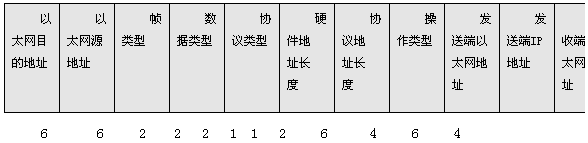
The first two fields in the Ethernet header are the destination and source addresses of the Ethernet. The special address whose destination address is all 1s is the broadcast address. All Ethernet interfaces on the same local area network must receive broadcast data frames. Next is the Ethernet frame type, 2 bytes long, indicating the type of data that follows. For ARP request or response, the value of this field is 0x0806. The hardware type field indicates the type of hardware address. A value of 1 indicates an Ethernet address. The protocol type field indicates the protocol address type to be mapped. A value of 0x0800 indicates an IP address. The hardware address length and protocol address length indicate the length of the hardware address and protocol address, respectively, in bytes. For ARP requests or replies to IP addresses on Ethernet, their values ​​are 6 and 4, respectively. The operation field indicates the type of operation, which can be ARP request (value 1), ARP reply (value 2). The remaining four fields are the sender's hardware address (Ethernet address), the sender's protocol address (IP address), the destination's hardware address, and the destination's protocol address.
For ARP requests, all other fields except the destination hardware address have padding values. When the system receives an ARP request message with the destination as the local machine, it fills in the hardware address, and then replaces the two sender addresses with the two destination addresses, and sets the operation field to 2, and finally Send it back.
From the above analysis, we can see that ARP data packets are expressed in C language as follows:
typedef struct _ARP_RHDR
{
UCHAR HardwareType [2]; // Data type, Ethernet is OX0001
UCHAR ProtocolType [2]; // Protocol type
UCHAR LengthOfHardware; // Hardware address length
UCHAR LengthOfProtocol; // Protocol address length
UCHAR OpCode [2]; // Operation type
UCHAR SrcMAC [6]; // Send Ethernet address
UCHAR SrcIP [4]; // Sender IP address
UCHAR DesMAC [6]; // Receiver Ethernet address
UCHAR DesIP [4]; // Receiver IP address
}
ARP_RHDR, * PARP_RHDR;
2.2 Using ARP spoofing to capture packets under the switched network
From the above analysis of the ARP protocol and the introduction of its principles, we can see that using ARP spoofing can make the network traffic of other machines in the subnet flow to the attacker machine, in order to enable them to use the network "normally" , The attacker must forward their data packets to the host they really should reach, which requires data forwarding. Therefore, to achieve normal network monitoring of switched Ethernet, it is necessary to use ARP spoofing combined with IP forwarding. In order to capture packets, two threads can be used: one to acquire, analyze, and forward data packets, and one to send ARP response packets at regular intervals.
In the network monitoring system, the implementation of HTTP access is based on the filtering of the target address. Through the analysis of each data field of the IP header, it is determined whether DesTInaTIon IP Address belongs to the set of restricted access set in the rule base. If it is, the system can adopt certain The means to prevent users from continuing to visit, the method used is to cut off or close the TCP connection. We can artificially construct a FIN message to send to the user, thereby closing the TCP connection between the user and the Web server, and prohibiting the user from accessing the URL address. The core function pcap_sendpacket of the Winpcap library provides the ability to bypass the normal network socket programming of the operating system and directly read and write the network card. After the important information of the TCP connection is analyzed, the forced interruption can be completed. When constructing an interrupted TCP message, the source and destination IPs need to be exchanged, the source and destination ports are exchanged, and then the flag position is RST, and then use pcap_sendpacket to send the message directly to achieve the purpose. Core implementation functions:
Void SendData (PIP_RHDR IpData)
{
PTCP_RHDR ptcpheader = (PTCP_RHDR) IpData-> Data;
int iRstFlag = ptcpheader-> Flags & 0x04;
if (iRstFlag = 0x04)
return;
...
SetMACToEther (MACADDR_SRC, & EtheRFrame, 0); // The source is sent to the local mac
SetMACToEther (MACCADDR_GATEWAY, & EtherFrame, 1); // The target is the mac of the default gateway
...
}
3 Software implementation and conclusion
The network monitoring software based on ARP spoofing uses virtual routing technology to realize the sending and receiving of messages. The software has been tested and basically achieved its intended purpose. Such a system can be used to monitor the switched Ethernet (such as campus network, enterprise network, etc.) that is currently used for various functions, so as to solve many inconveniences in network management, and thus realize network management. The ultimate goal-reasonable and full use of resources and the provision of reliable communication services.
Electric Car,Electric Shuttles,Best Small Electric Car,Four-Wheel Electric Vehicle
Jinan Huajiang environmental protection and energy saving Technology Co., Ltd , https://www.hjnewenergy.com