In recent years, as technology has advanced rapidly, consumer products have become increasingly intelligent. From smartphones and tablets to smartwatches, a wide range of smart devices now play a central role in daily life. However, with this technological progress comes a growing concern: information security. High-profile incidents such as the 2014 "Prism Gate" and the Apple iCloud data leak have raised public awareness about smartphone security. Additionally, CCTV's "3·15" campaign exposed numerous mobile apps that illegally collect user data and spread malicious software, further highlighting the risks users face.
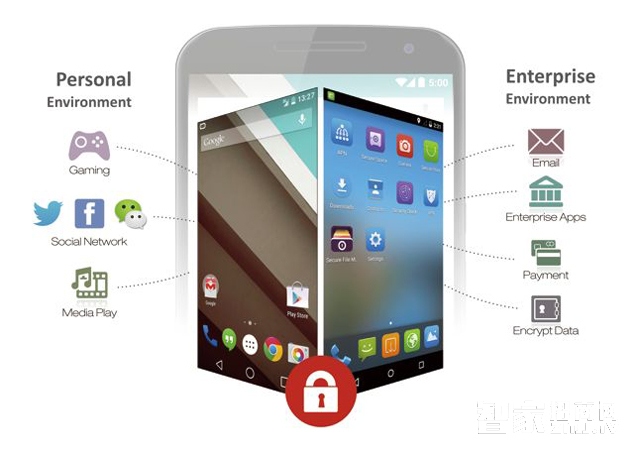
**Smart Terminal Security Issues**
Unlike traditional mobile devices, smart terminals pose far greater security risks. Any vulnerability in the operating system can allow hackers to deploy malware such as Trojans or worms, leading to privacy breaches, device malfunctions, or even network attacks. The open architecture of smart terminal systems allows developers to access APIs and platforms, which can be exploited by cybercriminals to create malicious applications. Furthermore, many OS providers secretly retain non-public APIs under the guise of system maintenance, creating backdoor risks that threaten user safety. In some cases, terminal manufacturers, OS providers, or app developers may also engage in unauthorized charges or data exploitation, negatively impacting users' financial interests.
Due to their advanced processing power and personalization features, smart devices store large amounts of sensitive user data—such as contact lists, messages, call logs, and card information. A single security breach can significantly affect both personal and professional life.
**Smart Terminal Security Measures – Software Protection**
1. **Passive Protection**: This involves using third-party security software to scan app signatures and limit application access to device resources. It is similar to traditional computer security measures.
2. **Active Protection**: In closed operating systems, third-party security tools often require high-level permissions to monitor and detect malicious activities. However, due to commercial restrictions, these tools are frequently blocked, limiting their effectiveness and stifling market competition. As a result, real-time protection and technical innovation are hindered.
**Smart Terminal Security Measures – Hardware Protection**
1. **Secure Boot**: This hardware-based feature ensures the integrity of the system during startup. If any unauthorized changes are detected in the system image, the boot process is automatically halted.
2. **Trusted Execution Environment (TEE)**: By leveraging hardware-based security, TEE provides an additional layer of protection that software alone cannot achieve. Organizations like the GlobalPlatform have developed secure architectures to address complex security challenges.
While information security remains a top priority for tech developers, the issue of smart terminal security has been widely recognized. Although challenges exist, continuous improvements ensure that smart devices remain safe and reliable. It's important to stay informed but not overly concerned—technology is constantly evolving to protect users.
Pet(Polyester) Membrane Switch,Membrane Keypad Switch,Metal Dome Membrane Keypad Switch,New Design Membrane Keypad
CIXI MEMBRANE SWITCH FACTORY , https://www.cnjunma.com