As early as 2007, the UK Tax and Customs Administration broke the "Disc Door" incident. As a result of the loss of the disc during the process of mailing the disc to the audit department, the personal information of 25 million people in nearly 7.5 million families was leaked. Danger. Due to the loss of the disc, the direct economic loss of the bank alone is as high as 500 million US dollars, which is a rare data breach in history. Therefore, the security of optical disc data is imminent, not only for enterprise users, but also for individual users.
This article refers to the address: http://
In response to the existence of such hidden dangers, as early as the application of the optical disc, related software and audiovisual enterprises have encrypted the optical discs, and then security vendors have introduced optical disc encryption technology. However, most of the optical disc encryption technologies are implemented by a combination of soft and hard or special track writing, which is not only highly demanding for professional technology, but also requires additional professional software tools or devices, and thus is not suitable for general user applications.
As the development of the optical storage industry gradually matures, relevant manufacturers are also involved in the optical disc security industry. In addition to the current software such as Power 2 Go, CD-protector, Nero, SecureBurn and CryptCd that support optical disc encryption technology, there are also a few optical storage vendors involved in this field to launch optical disc encryption solutions, such as Plextor "SecuRec" technology and LG's "lock code" technology.
ASUS Optical Storage also introduced its own encryption technology. It cooperates with CyberLink's "Power 2 Go Power Cooling" software to provide CD encryption technology, which is simpler, more flexible and more flexible. Compared with other technologies, ASUS CD encryption technology does not adopt the hardware encryption method with high application cost. Instead, it implements the encryption process in 128-bit software encryption format, eliminating the need for professional accessories and effectively reducing the cost of encryption applications. At the same time, the entire encryption process is the same as normal CD burning, and will not extend the burning time due to the addition of invalid data during the encryption process. In addition to supporting CD-format disc burning, it also supports the encryption of mainstream DVD and BD discs to meet the needs of different applications.
Below we use the ASUS ultra-thin king SDRW-08D1S-U and ultra-thin Wang Blu-ray combo SBC-04D1S-U two products to demonstrate the operation steps. The CD 2 encryption operation can be performed by the user's "Power 2 Go Power Cooling" software. The whole process is very simple, and the entire operation process can be completed according to the software prompts. From encryption to decryption browsing, you can do it in four steps.

set password
Click “Create Security Zone†in the interface, and then “Set Password for your encrypted file†will pop up. Enter the password, select "Hide the file name in the encrypted disc" and click the OK button to complete.
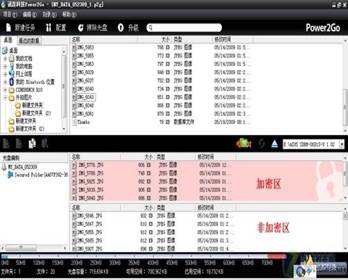
Select a document
After the password is set, the system automatically creates an encrypted area and an unencrypted area. Drag the encrypted file or folder you need to add into the encryption area, which is the red area in the picture, and drag the unencrypted file or folder into the non-encrypted area, which is the white area. When the disc is burned, the disc can only read the data information of the non-encrypted area without decryption, and the data information of the encrypted area must be read by decryption, otherwise it will be recognized as a special identifier.
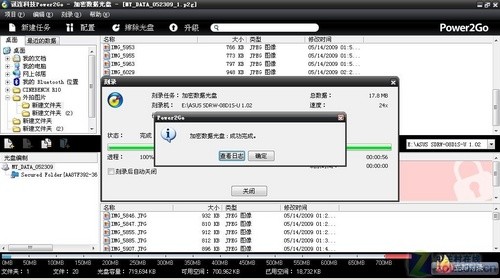
Burn file
Click the "Burn Now" button in the interface, wait a little, and the disc is burned.
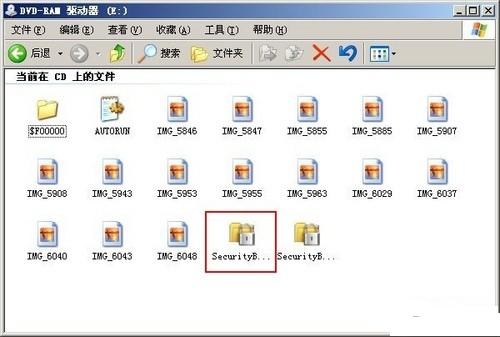
Browse to burn the disc, the browser built into the software will start. It was found that the previously unencrypted file already appeared in the root directory of the disc, and there was also a folder named "$F00000", which included all the contents of the encrypted area. Double-click to execute the first yellow encryption icon. Enter the previously set password and the previously encrypted file will appear.
As it moves throughout your home, Mopping Vacuum Robot can clean wooden floor, PVC floor and tile floor. Robot mopping vacuum use the artificial ground cleaning method to transfer the center of gravity of the body to the rag, to achieve Mopping Robot vacuum more powerful and clean. Specifically, Wet mop (remove stubborn stains) and dry wipe (wipe hair crumbs) are flexible to choose because of water tank.
Why you choose it?
(1)Two models of wet mop and dry wipe, mopping robot cleaner give you more choice.
(2)Automatic path planning, sweeping more thoroughly.
(3)Intelligent anti-collision and anti drop, a more suitable robot floor cleaner for you.


Mopping Vacuum Robot
Mopping Vacuum Robot,Floor Clean Robot,Mopping Robot,Mop Vacuum Cleaner Robot
Zhengzhou Bangmi Smart Technology Co., Ltd. , https://www.globalcleanrobot.com